Home Lab
Part 1 - Introduction
Why build a home lab?
Proactive Threat Detection: A lab allows you to proactively search for indicators of compromise (IOCs) and potential security threats within a controlled environment. By simulating real-world attack scenarios, you can actively hunt for suspicious activities, anomalies, or signs of compromise that may go unnoticed by traditional security monitoring tools.
Skill Development: Running a lab provides an opportunity to enhance the skills and expertise of cybersecurity professionals. It allows them to practice and refine their threat hunting techniques, learn new tools and methodologies, and gain hands-on experience in investigating and responding to potential security incidents.
Testing and Validation: The lab enables you to test and validate the effectiveness of your security controls, detection mechanisms, and incident response processes. By emulating various attack techniques and scenarios, you can assess if your defenses can detect, alert, and respond to these threats in a timely manner. This helps identify any gaps or weaknesses in your security posture and provides an opportunity to strengthen your overall defenses.
Overall, a home lab empowers users to take a proactive stance in detecting and responding to potential security threats. It helps improve the skills of cybersecurity professionals, validates security controls, fosters research and knowledge sharing, and ultimately enhances the organization’s overall security posture.
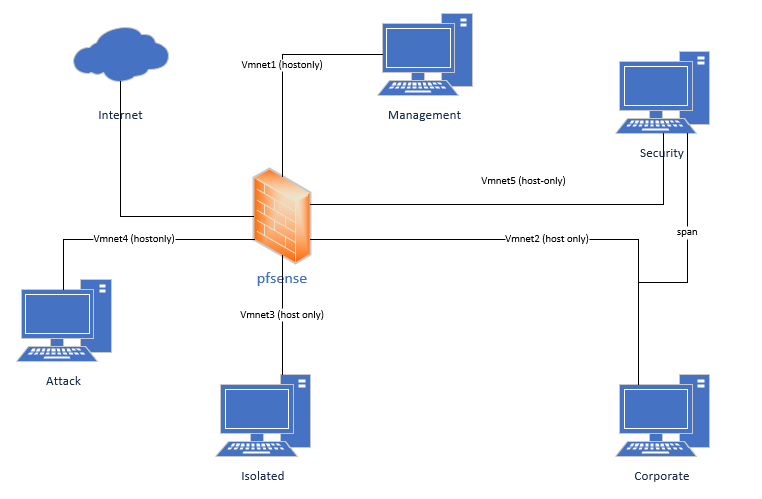
Part 2 - Topology
Part 3 - Firewall
PFSense (To be Updated)
Part 4 - Corporate
Active Directory
Windows 10
Ubuntu
Part 5 - Security
Security Onion (To be Updated)
Part 6 - Isolated
Note: Recommend to put any VMs that you will know will contain malicious files in this VLAN. And you don’t want to connect to the internet.
Renmux (link)
REMnux is a Linux toolbox designed for the purpose of dissecting and scrutinizing malicious software. This resource offers a meticulously selected compilation of free tools generated by the community, facilitating analysts in their malware investigations without the need to locate, set up, and customize these tools individually.
SIFT (link)
Taken from SANS website: “The SIFT Workstation is a collection of free and open-source incident response and forensic tools designed to perform detailed digital forensic examinations in a variety of settings.”
Additional Notes:
You can combine the two tools to create a VM for both forensics and malware analysis. (link)
Part 7 - Attack
ParrotOS
Kali Linux
Part 8 - Automated Adversary Emulation (To be updated)
Atomic Red Team
Caldera